The Domain Name System (DNS) is one of those invisible pieces of internet plumbing everyone relies on but few fully understand. At its simplest, DNS translates human-friendly names like firewallflow.com into machine-friendly addresses (IP addresses) that computers use to find each other. But behind that simple translation sits a global, distributed system with caching, hierarchies, security layers, and—yes—attack surfaces people can and do exploit. This article walks through DNS from the basics to advanced topics, explains common DNS records and queries, shows how resolution works step-by-step, covers security and hardening, and gives practical troubleshooting commands you can use right now.

1. What is DNS?
DNS stands for Domain Name System. It’s like the internet’s phonebook: when you want to call a friend you look up their name to find their number; when your browser wants to load example.com, it asks DNS for the IP address. The reason DNS exists is convenience and readability—humans remember names but machines route using numeric IP addresses.
DNS is intentionally distributed and hierarchical. Instead of one central database, DNS uses many servers organized in a tree-like structure. This design gives DNS scalability (it can handle billions of lookups), redundancy (no single point of failure), and performance (locally cached answers reduce latency).
2. How DNS Works — step-by-step
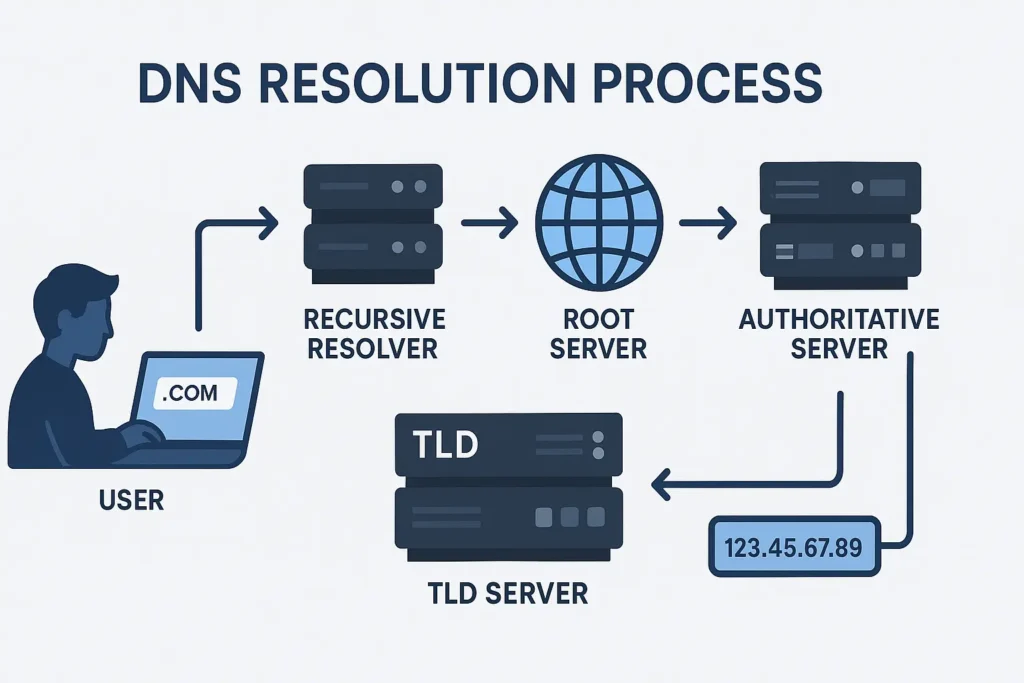
Imagine you type www.firewallflow.com into your browser. Here’s what typically happens next:
- Your operating system checks its local DNS cache to see if it already knows the IP. If it does, resolution ends quickly.
- If not cached locally, the query goes to your configured recursive resolver—often your ISP’s resolver or a public resolver like Google DNS (
8.8.8.8) or Cloudflare (1.1.1.1). - The recursive resolver may have the answer cached; if not, it performs a sequence of lookups starting at the root servers.
- Root servers tell the resolver which TLD (top-level domain) servers to ask for
.com. - The resolver queries the
.comTLD servers, which respond with the authoritative name server forfirewallflow.com. - The resolver queries that authoritative server and receives the final answer: the IP address for
www.firewallflow.com. - The resolver returns the IP to your OS, which connects to the web server and loads the site. The resolver and your OS usually cache the answer for the record’s TTL (time-to-live) to speed up future lookups.
This whole sequence usually takes milliseconds. Caching and local resolvers make DNS fast in practice because most answers are already stored closer to the client.
3. Key components of DNS
DNS has a few roles and server types that are useful to understand:
- Recursive resolver (resolver): The server that takes a client’s query and does the work of asking other DNS servers until it finds the final answer. End users and devices typically talk to a resolver.
- Root name servers: The highest level in the DNS hierarchy. They don’t know domain IPs but direct queries to the appropriate TLD servers (
.com,.net,.in, etc.). - TLD name servers: These servers manage information for top-level domains and point resolvers to authoritative servers for a specific domain.
- Authoritative name servers: The source of truth for a domain’s DNS records. They contain the actual records (A, MX, NS, etc.) for the domain.
- Caching: Resolvers cache answers for the TTL period. Caching reduces latency and global query load but also creates propagation delays when records change.
4. DNS records — what each one does
DNS stores many record types. Each record has a purpose and a TTL that controls how long it’s cached. Here are the most important ones:
A record (Address) — Maps a domain to an IPv4 address. Example: www.firewallflow.com → 192.0.2.1 (documentation IP). When your browser needs to connect over IPv4, it uses the A record.
AAAA record — Same as A but for IPv6 addresses. Example: www.example.com → 2001:db8::1 (documentation IPv6).
CNAME record (Canonical Name) — Creates an alias from one name to another. For example, blog.firewallflow.com CNAME -> host.examplecdn.com. CNAMEs cannot coexist with other record types at the same name (e.g., you cannot have a CNAME and an A record on the same label).
MX record (Mail Exchange) — Directs email to mail servers for a domain. Each MX has a priority. Mail servers check MX records to decide where to deliver mail.
NS record (Name Server) — Specifies which name servers are authoritative for a domain or subdomain. These are what TLD servers return to point resolvers to the authoritative zone.
SOA record (Start of Authority) — Holds metadata about a DNS zone: the primary name server, an administrative contact, the zone serial number, and timing parameters for zone transfers and caching.
TXT record — Stores arbitrary text. Commonly used for SPF, DKIM public keys, and domain ownership verification.
PTR record (Pointer) — Used for reverse DNS: maps an IP address back to a hostname. Important for email anti-spam measures.
SRV record (Service) — Specifies hosts and ports for specific services (e.g., SIP or XMPP). Useful for services that need service discovery.
There are other specialized records (DNSKEY, RRSIG, DS) used by DNSSEC; these show up when DNSSEC is enabled and implement cryptographic validation.
5. Types of DNS queries
DNS queries can be recursive, iterative, or non-recursive:
Recursive query: The client asks a resolver for the final answer and expects the resolver to perform all required steps to reach the authoritative answer. Typical client → resolver interactions are recursive.
Iterative query: The resolver asks a server (like root or TLD) and the server returns the best information it has—often a referral to another server. The resolver may then query that referred server. Root and TLD servers typically respond iteratively.
Non-recursive query: The server already has the answer cached or is authoritative for the name, so it responds immediately without further lookups.
Understanding these query types helps when troubleshooting why a resolver is making many external queries or why responses are slower.
6. Types of DNS servers (by role)
While we already described them in components, thinking of servers by role clarifies operations:
- Stub resolver: A minimal client-side resolver, typically part of an OS or application, that sends queries to a configured recursive resolver.
- Recursive resolver (caching resolver): Performs the full resolution process and caches results.
- Authoritative name server: Holds actual DNS data for zones and responds authoritatively.
- Forwarding resolver: Instead of resolving itself, this resolver forwards client queries to another resolver (common in corporate networks to funnel DNS through security controls).
- Hidden master / secondary (slave) servers: In zone replication setups, one server (master) holds the writable zone file while secondaries fetch copies via zone transfer. Secondaries are authoritative but pull from the master.
7. Why DNS matters in modern networking
DNS is critical for many reasons beyond simply looking up web addresses:
User experience: Easy-to-remember hostnames are how most people access services. If DNS is slow or broken, users can’t reach services.
Load balancing & CDNs: Content delivery networks and load balancers use DNS to distribute traffic across geographically distributed servers (for example, using short TTLs to steer traffic).
Email routing: MX records determine how email flows. Broken DNS can cause mail delivery failures.
Service discovery: Many cloud and microservice platforms rely on DNS for discovery and configuration.
Security & policy enforcement: Modern network security frequently inspects DNS traffic, filters malicious domains, and logs DNS activity as a signal for threat detection.
Because DNS is a choke point for name-based access and controls, attackers often target DNS to disrupt services or redirect traffic.
8. DNS security: common threats
DNS is both a target and a vector for attacks. Common threats include:
DNS cache poisoning (spoofing): An attacker injects a false DNS response into a resolver’s cache so that subsequent queries return the wrong IP (for example, pointing bank.example at an attacker-controlled host). This lets attackers perform phishing or man-in-the-middle attacks.
DNS hijacking / compromise: Attackers gain control of a domain’s authoritative records (often via stolen credentials at the registrar) and change DNS records to route traffic elsewhere.
DDoS attacks against DNS infrastructure: Overwhelming authoritative servers or resolvers can take services offline. Distributed reflection/amplification attacks using DNS are also common—attackers send small spoofed queries to open resolvers that return much larger responses to the victim, amplifying traffic.
Rogue or malicious resolvers: If clients use a compromised or malicious resolver, their DNS traffic can be observed, censored, or manipulated.
DNS tunnelling: DNS traffic can be abused to tunnel other data (exfiltration or C2 channels) because DNS is often allowed through firewalls.
Because DNS is so foundational, attacks on DNS can have outsized effects on availability, confidentiality, and integrity.
9. DNS security solutions and best practices
There’s no single fix, but several strong measures reduce DNS risk:
DNSSEC (Domain Name System Security Extensions): DNSSEC adds digital signatures to DNS records, letting resolvers cryptographically verify that DNS responses come from the authoritative owner and haven’t been tampered with. DNSSEC protects integrity and authenticity (it does not encrypt DNS traffic).
DoH (DNS over HTTPS) and DoT (DNS over TLS): These protocols encrypt DNS queries between clients and resolvers, protecting privacy and preventing on-path observers from seeing which domains a client queries. They reduce eavesdropping but can complicate network monitoring and filtering if improperly managed.
Use reputable resolvers and enable validation: Configure resolvers to perform DNSSEC validation where possible, and use trusted public resolvers or properly managed internal resolvers.
Restrict zone transfers: Authoritative servers should only allow zone transfers (AXFR/IXFR) to specified IPs (secondary servers) to prevent theft of your DNS zone content.
Harden registrar access: Use strong passwords, MFA, and registrar locks to protect domain registration settings. Many “hijack” incidents stem from compromised registrar accounts.
Use multiple authoritative name servers and Anycast: Redundancy across providers and Anycast routing helps absorb DDoS and improves availability.
Monitor DNS logs and set alerts: Look for unusual record changes, sudden spikes in NXDOMAIN responses, or unexpected queries that could signal tunnelling or reconnaissance.
Rate limiting and response policy zones (RPZ): Rate-limit responses to reduce amplification potential and use RPZ to block known malicious domains.
Segment and control DNS on the network: For enterprise networks, forward client queries through resolvers you control (forwarding resolvers), inspect DNS traffic, and consider split-horizon DNS to separate internal name resolution from public resolution.
Combining these practices significantly raises your DNS security posture.
10. Troubleshooting DNS — practical commands and tips
When DNS breaks, a few tools quickly reveal what’s wrong.
dig (Linux/macOS) is the go-to flexible DNS debugging tool. Examples:
# Query an A record
dig A firewallflow.com +short
# Trace resolution from the root down (shows the path)
dig +trace firewallflow.com
# Query a specific resolver (e.g., Google)
dig @8.8.8.8 firewallflow.com Anslookup works on Windows and many systems:
nslookup
> server 8.8.8.8
> set type=mx
> firewallflow.comhost is a simpler resolver utility:
host -t txt firewallflow.comFor live capture and deeper troubleshooting, tcpdump or Wireshark can inspect DNS packets to confirm whether queries are sent over UDP/TCP or whether DoT/DoH is in use. Use these commands to check for TTL issues or mismatched authoritative answers. Also check local OS caches (e.g., systemd-resolve --flush-caches on systemd systems or ipconfig /flushdns on Windows) and test against multiple resolvers (your ISP’s, 8.8.8.8, 1.1.1.1) to see if issues are cache-related.
If emails fail, check MX records and whether reverse DNS (PTR) matches the sending IP; many email receivers reject mail without matching reverse DNS.
11. Real-world examples and common pitfalls
A few practical examples help crystallize DNS behavior:
Public resolvers: Google DNS (8.8.8.8) and Cloudflare (1.1.1.1) are widely used for performance and privacy. They are recursive resolvers that cache answers and perform DNSSEC validation if requested.
CDNs & geo-routing: Many CDNs use DNS to direct users to the nearest edge server. Short TTLs allow rapid changes in routing if load shifts.
Outages matter: History shows that when a major DNS provider or registrar is attacked or misconfigured, large portions of the web become unreachable. That’s why redundancy, multiple providers, and registration safeguards are critical.
Propagation misunderstandings: When you change a DNS record, some users might still be directed to the old IP until caches expire (TTL). Plan low-TTL changes ahead of major migrations to avoid surprises.
12. Practical recommendations for network and security teams
If you manage networks or run websites, here are practical, actionable suggestions:
- Use DNSSEC where possible and monitor validation status.
- Deploy multiple authoritative servers across providers and use Anycast for resilience.
- Configure internal resolvers and forward external queries through controlled resolvers to enforce policy and logging.
- Harden registrar accounts and enable domain locks where offered.
- Monitor DNS logs and set alerts for unusual changes or traffic patterns.
- Consider encrypted DNS (DoH/DoT) for user privacy but plan how monitoring and parental controls will continue to work.
- Limit zone transfers by IP and protect secondary servers.
- Implement rate limiting on DNS servers and filter/refuse open recursive queries to prevent abuse.
These steps balance availability, performance, and security.
13. Conclusion
DNS quietly powers the address-book function of the internet. It’s fast, distributed, and essential for everything from website access and email delivery to content delivery networks and service discovery. But DNS is not just a convenience—it’s a critical infrastructure with real security concerns. Understanding DNS records, the resolution process, and the common attack vectors lets you design more resilient systems and respond faster when issues occur.
📌 Read More
- What Is HTTP? – Explore the foundation of web communication and how HTTP enables browsers and servers to exchange information.
- What Is the Internet? – Understand the global network of interconnected devices and how the Internet facilitates data sharing and communication.
- Application Layer in OSI & TCP/IP Models – Dive into the topmost layer of the OSI and TCP/IP models, responsible for end-user services like web browsing and email.
Cybersecurity blogger with a focus on firewalls, network security, and tech trends making security simple for everyone, from IT pros to curious minds.