
What is WAF?
A Web Application Firewall (WAF) is an application firewall designed to filter, monitor, and block HTTP traffic to and from a web application. A WAF is defined by its ability to filter the content of specific web applications while allowing or blocking access based on predefined security rules (policies).
By deploying a WAF in front of a web application, a shield is placed between the web application and the Internet. A WAF is a type of reverse proxy that protects the server from exposure by having clients pass through the WAF before reaching the server. This contrasts with a proxy server, which protects client identities.
It protects web applications from a variety of application-layer attacks such as cross-site scripting (XSS), SQL injection, and cookie poisoning. These attacks are among the top causes of data breaches and application vulnerabilities. A properly configured WAF can block such attacks and prevent data exfiltration.
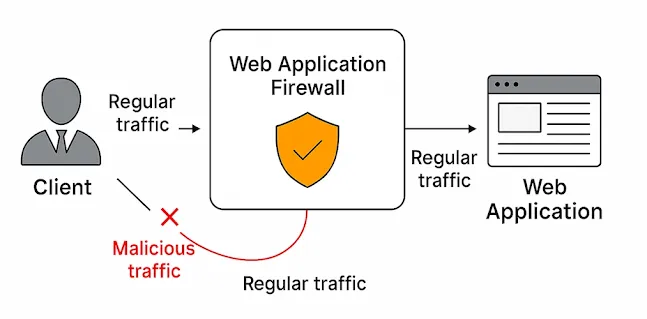
How It Works
A WAF protects your web apps by filtering, monitoring, and blocking malicious HTTP/S traffic traveling to the application, and prevents any unauthorized data from leaving the app. It does this by applying a set of rules that determine what traffic is safe and what should be blocked.
WAFs act as reverse proxies, meaning they sit in front of the web server and intercept incoming traffic. They inspect key components such as HTTP methods (GET, POST, PUT, DELETE), headers, query strings, cookies, and request bodies to identify threats. If a threat is detected, the WAF blocks the request and can alert the security team or log the event for analysis.
They are available as software, hardware appliances, or cloud-based services. Rules can be customized based on the specific needs of the application. While some WAFs require manual rule updates, advanced ones utilize machine learning to update automatically, adapting to new threats in real-time.
Types of WAF

WAFs can be implemented in the following ways:
| Type | Description | Pros | Cons |
|---|---|---|---|
| Network-Based | Hardware appliance installed locally | Low latency, high performance | Expensive, physical upkeep |
| Host-Based | Software integrated into the application stack | Customizable, cost-effective | Resource-heavy, complex setup |
| Cloud-Based | Delivered as a service via cloud providers | Scalable, easy to deploy | May introduce latency |
1. Network-Based WAF
- Typically hardware-based
- Installed locally on the network
- Offers minimal latency
- Requires maintenance of physical equipment
- Most expensive option
2. Host-Based WAF
- Integrated into the software of the web application
- Highly customizable
- Consumes server resources
- Complex to implement and maintain
- Requires engineering effort and incurs operational costs
3. Cloud-Based WAF
- Delivered as a service (SaaS model)
- Easy and fast to deploy (often just a DNS change)
- Affordable with subscription-based pricing
- Always updated with the latest threat intelligence
- No hardware or complex configuration needed
Advantages of WAF
- Cross-Site Scripting (XSS) Protection: Prevents injection of malicious scripts into user browsers.
- SQL Injection Mitigation: Stops attempts to execute unauthorized queries on the application's backend database.
- Session Hijacking Defense: Secures web sessions from being hijacked by attackers through session ID theft.
- DDoS Attack Mitigation: Reduces the risk of distributed denial-of-service attacks by filtering high volumes of malicious requests.
- WAFs can protect applications without needing source code access.
- Cloud WAFs offer quick deployment and provide virtual patching—allowing users to instantly apply security fixes while the development team works on a permanent fix.
Importance of WAF
WAFs are vital for any organization providing services or storing sensitive data online. Financial institutions, e-commerce platforms, healthcare services, and social media companies all rely on web applications that must be protected from threats.
WAFs are essential for:
- Protecting sensitive data (e.g., login credentials, payment info)
- Maintaining compliance (e.g., PCI DSS)
- Preventing downtime from DDoS or zero-day exploits
- Securing APIs and mobile apps that provide services or store sensitive data online
WAF Vendors
Various vendors offer WAF solutions, each with different features. Notable ones include:

WAF vs Firewall & IPS
| Feature | WAF | Traditional Firewall |
|---|---|---|
| OSI Layer | Layer 7 (Application) | Layer 3/4 (Network/Transport) |
| Focus | Web traffic and app vulnerabilities | IP, port, and protocol filtering |
| Threats Blocked | XSS, SQLi, CSRF, etc. | Unauthorized access, malware |
| Configuration | Rule-based or ML-driven | Rule-based |
Intrusion Prevention System (IPS)
- Broader security product than WAF
- Signature and policy-based detection
- Protects multiple protocol types (DNS, SMTP, SSH, FTP)
- Primarily works at OSI Layers 3 and 4
- Can perform basic application-layer filtering
Next-Generation Firewall (NGFW)
- Protects outbound user traffic to the internet
- Enforces user-based policies
- Offers URL filtering, anti-malware, antivirus, and built-in IPS
- Typically forward proxies (used by client-side)
Web Application Firewall (WAF)
- Focuses solely on application-layer (Layer 7) HTTP/S traffic
- Reverse proxy (used by server-side)
- Understands user sessions and specific web application contexts
- Defends against OWASP Top 10 vulnerabilities:
- Injection attacks
- Broken authentication
- Sensitive data exposure
- XML External Entities (XXE)
- Broken access control
- Security misconfigurations
- XSS
WAF Mitigation
So how, exactly, does a WAF mitigate all those vulnerabilities? There are three primary methods a WAF uses to detect and prevent web attacks: deny/allow requests, inspect and reject, and signatures.
Deny/Allow Requests
This method functions similarly to traditional firewall logic. Requests are either permitted or blocked based on specific criteria. This could be as simple as blocking by IP address or as advanced as allowing/disallowing specific HTTP methods such as OPTIONS or PUT. This basic filtering is effective for known bad actors or common exploit vectors.
Signatures
Signatures are predefined patterns used to detect known malicious behaviors. Just like antivirus tools rely on virus definitions, WAFs use signatures to identify and block known threats. These can be:
- Vendor-managed: Regularly updated by the WAF provider.
- User-defined: Custom rules created based on unique application behavior.
Inspection
Inspection allows granular control of requests and responses. Since HTTP is a flexible, text-based protocol, inspection is necessary to analyze all parts of a request — including headers and payloads — for anomalies or malicious code.
There are two ways to use inspection:
- Known Headers: Examining specific headers (e.g., User-Agent, Content-Type) for abnormal or malicious values.
- Payload Inspection: Analyzing the body of the request (e.g., form inputs, JSON data) for harmful scripts or SQL injection attempts.
Key Features to Look For
- Real-time traffic analysis
- Custom rule sets
- Bot mitigation
- Rate limiting
- Logging and alerting
- Integration with SIEM tools
Best Practices for Deployment
- Place WAF in front of public-facing apps
- Regularly update rule sets and signatures
- Monitor logs and tune policies to reduce false positives
- Combine with other security layers (e.g., IDS/IPS, DLP)
Conclusion
A Web Application Firewall is a critical component in modern web security architecture. It complements other security tools by focusing on application-layer vulnerabilities, often the most exploited in today's threat environment. By using a WAF, organizations can better protect their web applications, customer data, and maintain trust with users.
As attacks grow more sophisticated, implementing a WAF is not just best practice—it’s essential.
Stay secure. Stay protected. Use a WAF.
Frequently Asked Questions (FAQs) about WAF
What is a Web Application Firewall (WAF)?
A WAF is a security solution that filters, monitors, and blocks malicious HTTP/S traffic to and from a web application. It protects applications from common threats like SQL injection, cross-site scripting (XSS), and cookie poisoning.
How does a WAF work?
WAFs act as a reverse proxy between users and the web server. They inspect HTTP requests and block or allow traffic based on rules or machine learning algorithms to prevent attacks on the application layer.
What are the main types of WAF?
The three main types of WAFs are network-based, host-based, and cloud-based. Network-based WAFs offer high performance, host-based WAFs provide deep customization, and cloud-based WAFs are scalable and easy to deploy.
Why do websites need a WAF?
Websites need a WAF to block threats that target web application vulnerabilities, protect user data, prevent downtime from DDoS attacks, and comply with standards like PCI DSS.
What are some popular WAF vendors?
Some of the top WAF vendors include Cloudflare, Akamai, AWS WAF, Imperva, F5, Fortinet, Barracuda, Radware, and Palo Alto Networks. Each offers unique features for web application protection.
