🌐 Understanding the Application Layer
The Application Layer is the seventh and topmost layer of the OSI (Open Systems Interconnection) model. It serves as the interface between the end-user and the network. While it doesn’t include the actual applications themselves, it facilitates communication between software applications and lower-layer network services.
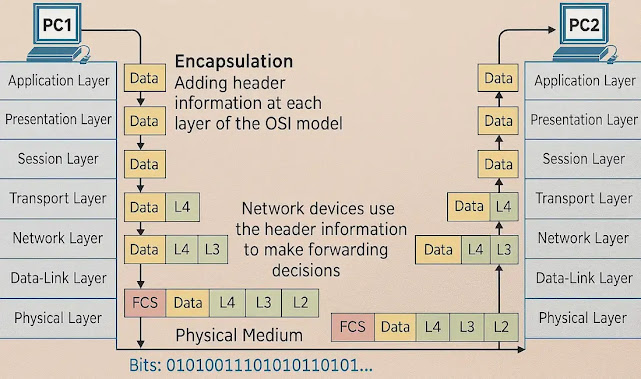
It handles protocols and services that support user-facing functionalities. These include software for email, file transfer, remote login, and web browsing. Since it deals directly with end-user applications, this layer is vital in ensuring a seamless user experience. The diagram below illustrates the position of the Application Layer within the OSI and TCP/IP models..
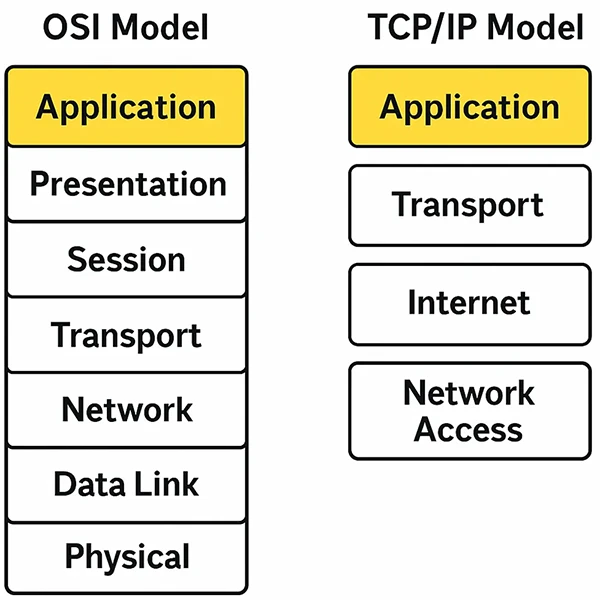
🧱 Role of the Application Layer
The Application Layer enables applications running on different systems to communicate with each other across a network. It provides services directly to the user or application, such as:
- Email (SMTP, IMAP, POP3)
- File transfers (FTP, TFTP)
- Web browsing (HTTP, HTTPS)
- Remote desktop (Telnet, SSH)
- DNS (Domain Name System)
- Network management protocols (SNMP)
This layer is responsible for:
- Identifying communication partners
- Determining resource availability
- Synchronizing communication
- Ensuring communication integrity and privacy (when combined with secure transport protocols)
- Managing user authentication and authorization in web-based apps
It abstracts the lower layers and allows users to interact with network services via graphical or command-line interfaces.
📦 Protocols Used in the Application Layer
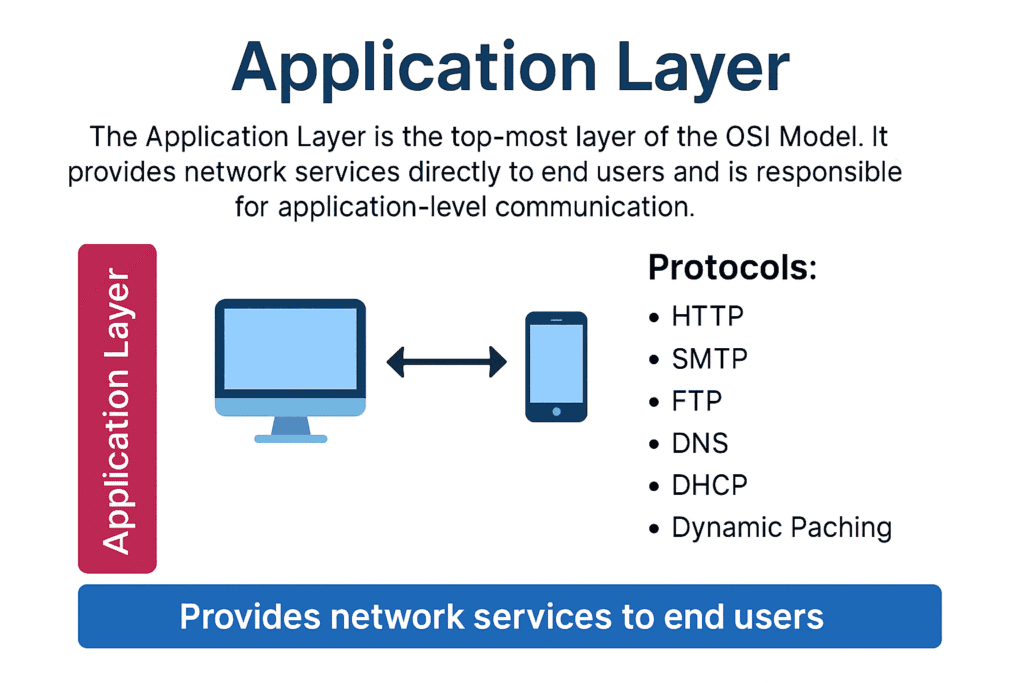
Here are some widely used Application Layer protocols:
| Protocol | Description |
|---|---|
| HTTP/HTTPS | Foundation of data communication for the web (Hypertext Transfer Protocol). HTTPS adds encryption for secure communication. |
| FTP | Used to transfer files between client and server over a network. |
| SMTP | Simple Mail Transfer Protocol, used to send emails. |
| POP3 | Post Office Protocol version 3, used to retrieve emails from a mail server. |
| IMAP | Internet Message Access Protocol, used to access and manage email on a remote mail server. |
| DNS | Domain Name System, translates human-readable domain names into IP addresses. |
| Telnet | Allows users to access remote devices using a command-line interface. |
| SSH | Secure Shell, a secure version of Telnet using encryption for remote login. |
| SNMP | Simple Network Management Protocol, used for monitoring and managing network devices. |
Other examples include:
- LDAP for directory services
- RDP for remote desktop access
- NFS and SMB for network file sharing
⚙️ Working of Application Layer
The Application Layer works by enabling applications to communicate over the network. Here’s a simplified breakdown:
- User Interaction: A user interacts with an application, such as a web browser or email client.
- Protocol Invocation: The application invokes an appropriate protocol (like HTTP for web browsing, SMTP for email).
- Data Packaging: The protocol formats the data according to predefined rules, adding headers and metadata as needed.
- Session Setup: The application may negotiate settings or permissions with the receiving system (e.g., via HTTP headers or authentication tokens).
- Data Transmission: The packaged data is handed to the Presentation and Session layers, eventually reaching the Transport and Network layers for transmission.
- Response Handling: On the receiving end, the Application Layer interprets the incoming data and delivers it to the target application (e.g., displaying a web page or delivering an email).
This working process ensures reliable, user-friendly, and secure communication across distributed systems.
🛡️ Security at the Application Layer
Because the Application Layer is closest to the user, it is also the most exposed to threats. Common vulnerabilities and attacks include:
- Phishing and Social Engineering
- SQL Injection
- Cross-Site Scripting (XSS)
- Man-in-the-Middle Attacks (MitM)
- Session Hijacking
Security measures include:
- Using HTTPS instead of HTTP
- Implementing WAF (Web Application Firewall)
- Validating user input
- Encrypting sensitive data
- Applying regular software patches
- Employing multi-factor authentication (MFA)
- Rate-limiting and CAPTCHA to prevent automated abuse
🧠 Importance of the Application Layer
The Application Layer plays a critical role in:
- Supporting end-user activities like browsing, emailing, and file sharing
- Allowing developers to create network-aware applications
- Ensuring proper data formatting, reliability, and service matching
It serves as the foundation for user-facing functionality and bridges the gap between human inputs and machine-level network communication.
In modern networking, cloud computing and SaaS (Software as a Service) have made the Application Layer even more crucial. Services like Google Workspace, Microsoft 365, and Salesforce all operate extensively at this layer.
🧩 Application Layer in the OSI vs. TCP/IP Model
While the OSI model separates the Application, Presentation, and Session layers, the TCP/IP model combines these into a single Application Layer. In practical networking, the TCP/IP model is more commonly referenced.
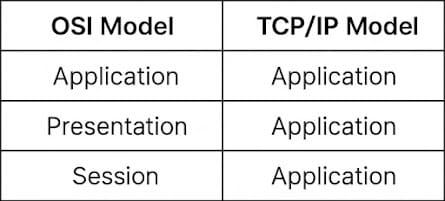
This simplification is more aligned with how protocols are actually implemented in modern systems.
📌 Conclusion
The Application Layer is the cornerstone of user interaction with the network. It supports essential functions such as file transfers, web services, and email communication. Understanding this layer is vital for network administrators, developers, and security professionals alike. By learning how data is managed and secured at this level, we can build more resilient, user-friendly, and secure networked applications.
Whether you’re configuring a web server, setting up an email client, or developing an API, you’re working with the Application Layer—making it one of the most critical layers in modern networking.
❓ Frequently Asked Questions (FAQ)
What is the function of the Application Layer?
The Application Layer facilitates communication between user applications and the lower layers of the network by using various protocols.
Which protocols operate in the Application Layer?
Common protocols include HTTP, HTTPS, FTP, SMTP, DNS, Telnet, SSH, SNMP, IMAP, POP3, and more.
How does the Application Layer differ in the OSI and TCP/IP models?
In OSI, the Application Layer is separate from Presentation and Session layers, whereas TCP/IP combines all three into a single Application Layer.
Is the Application Layer responsible for data encryption?
No, encryption is typically handled by the Presentation Layer or protocols like HTTPS, but the Application Layer can request secure connections.
Why is the Application Layer vulnerable to attacks?
Being closest to the user, it’s exposed to threats like phishing, SQL injection, and cross-site scripting if not properly secured.
📎 Related Posts
Want to understand how the Application Layer fits into the broader networking stack? Check out these foundational articles:
Cybersecurity blogger with a focus on firewalls, network security, and tech trends making security simple for everyone, from IT pros to curious minds.